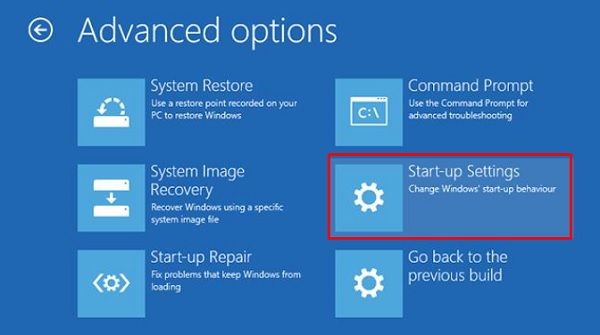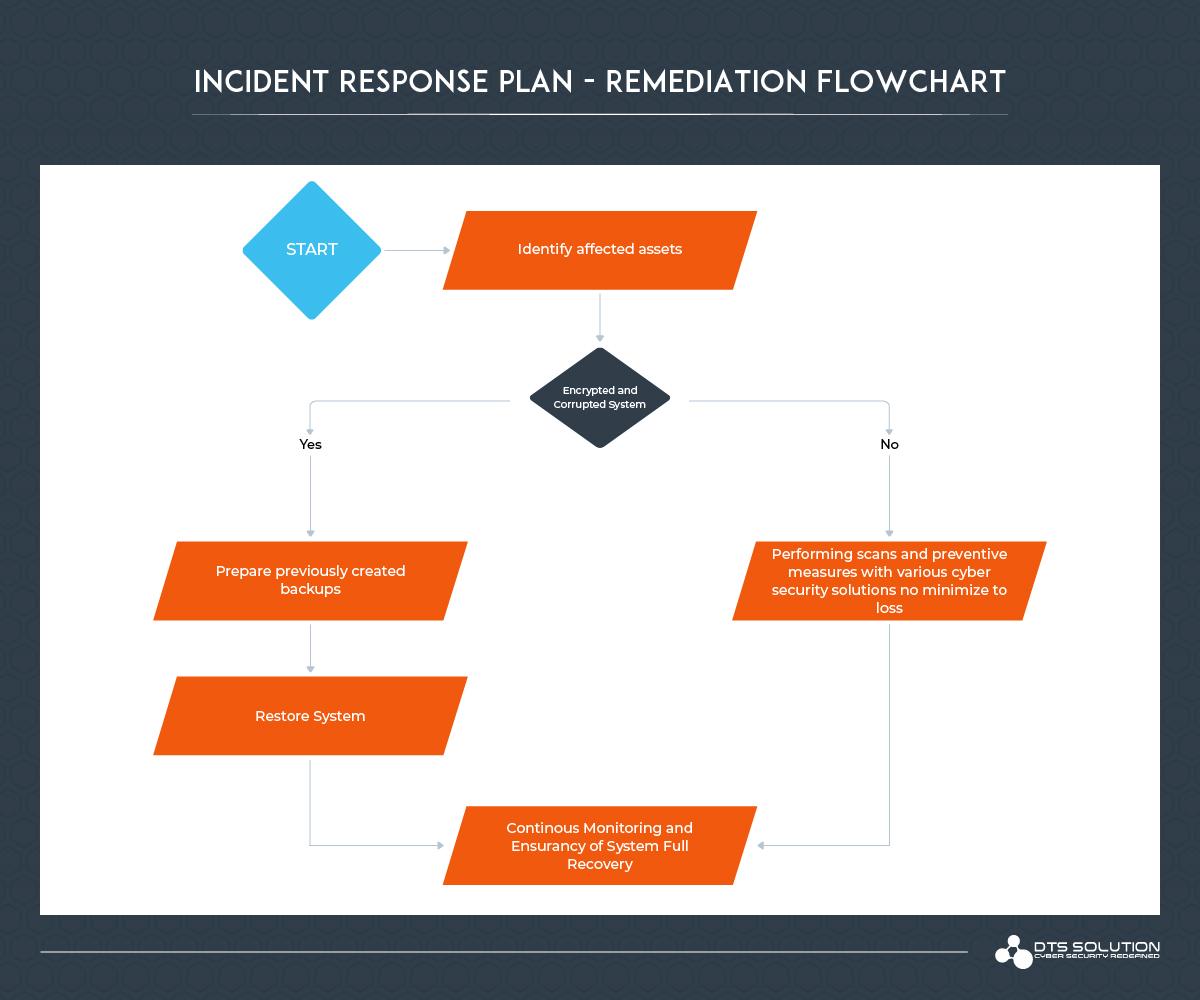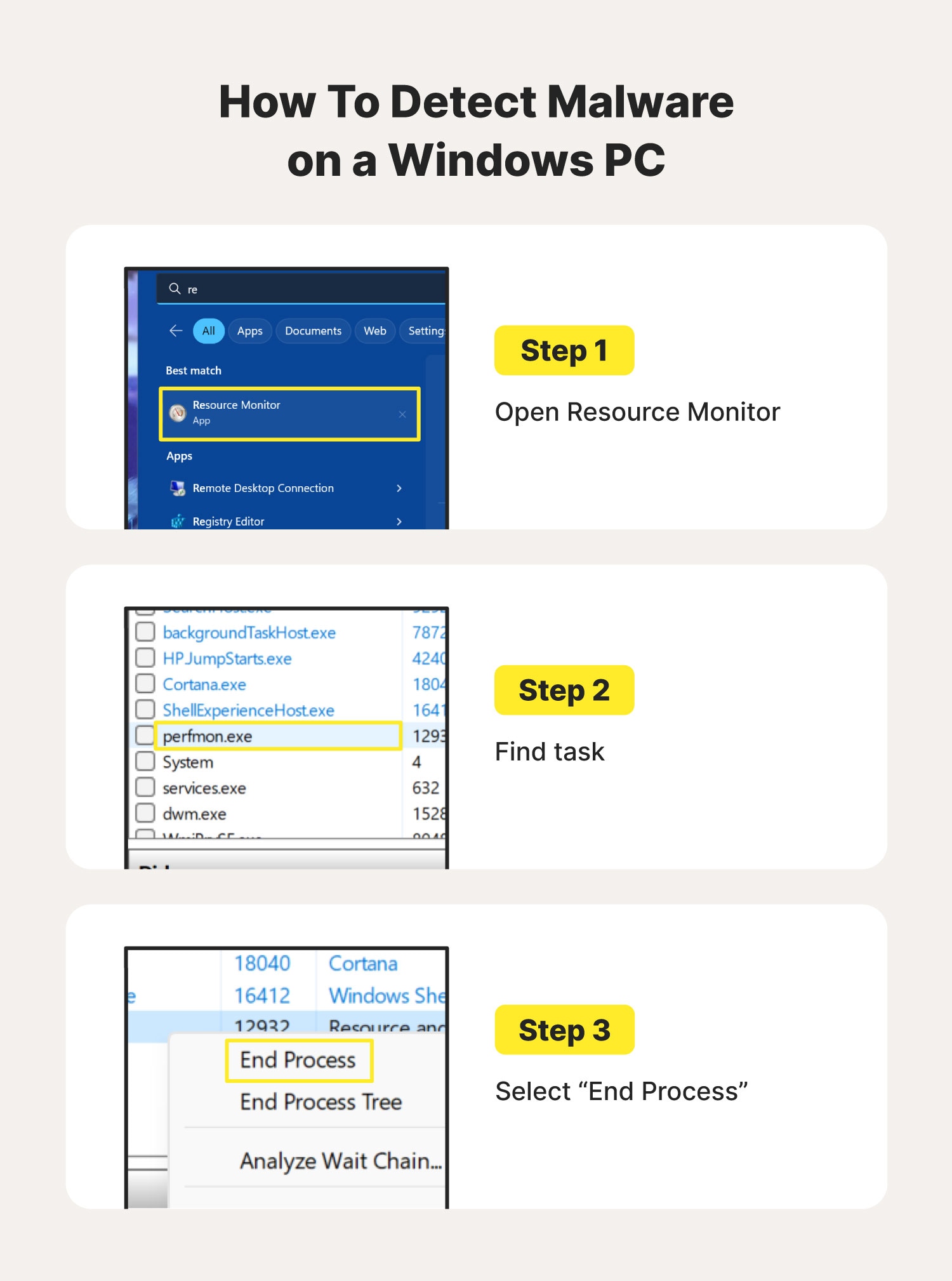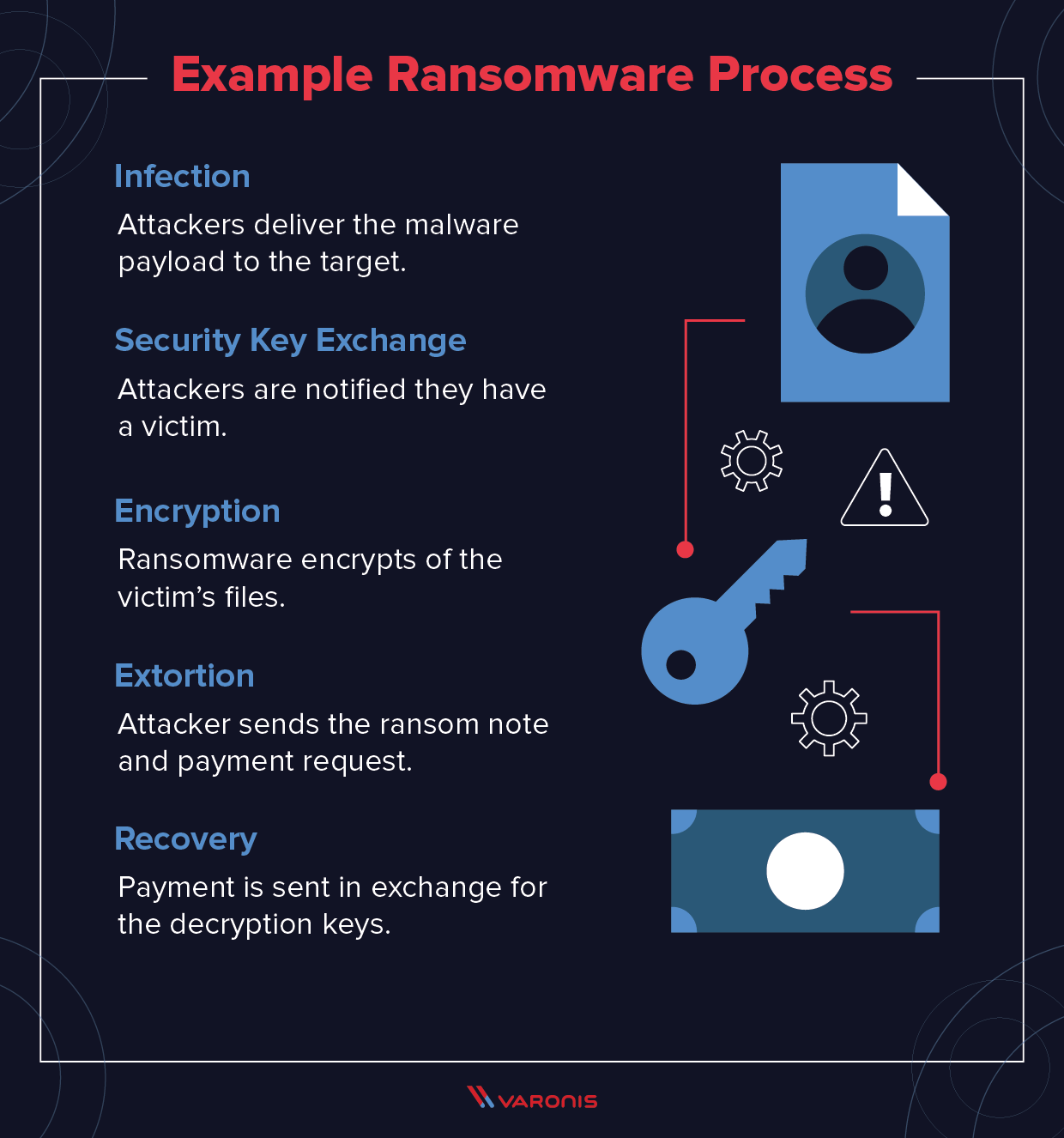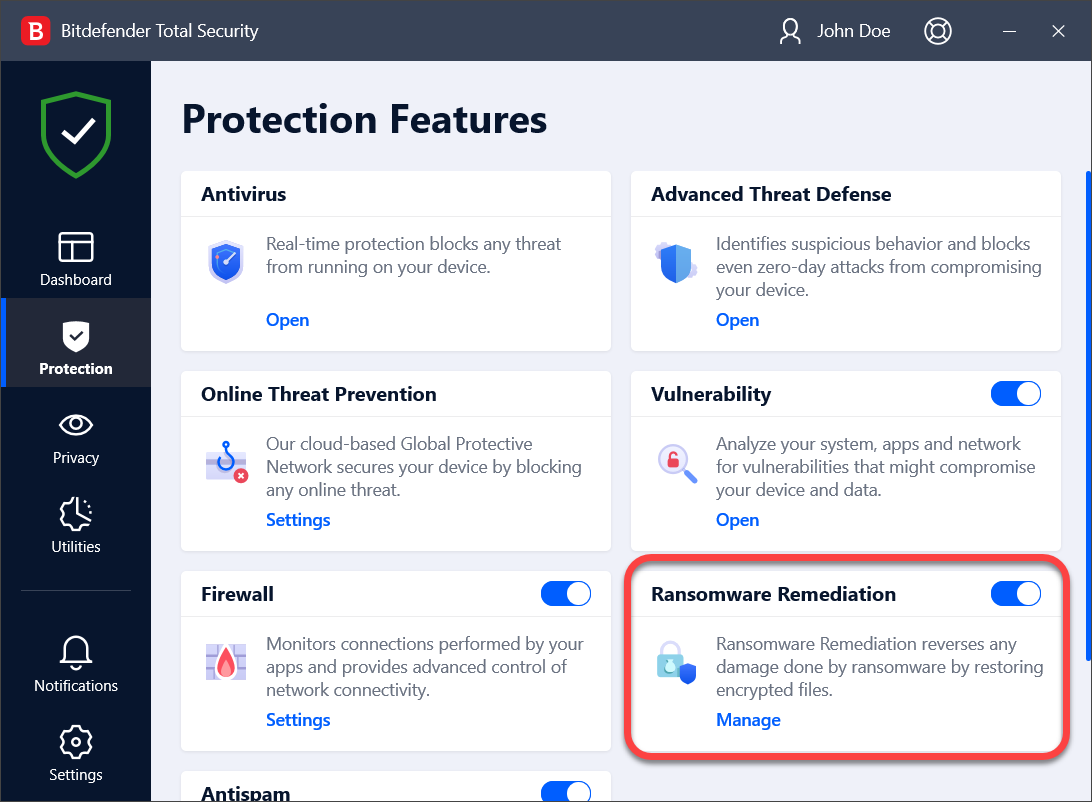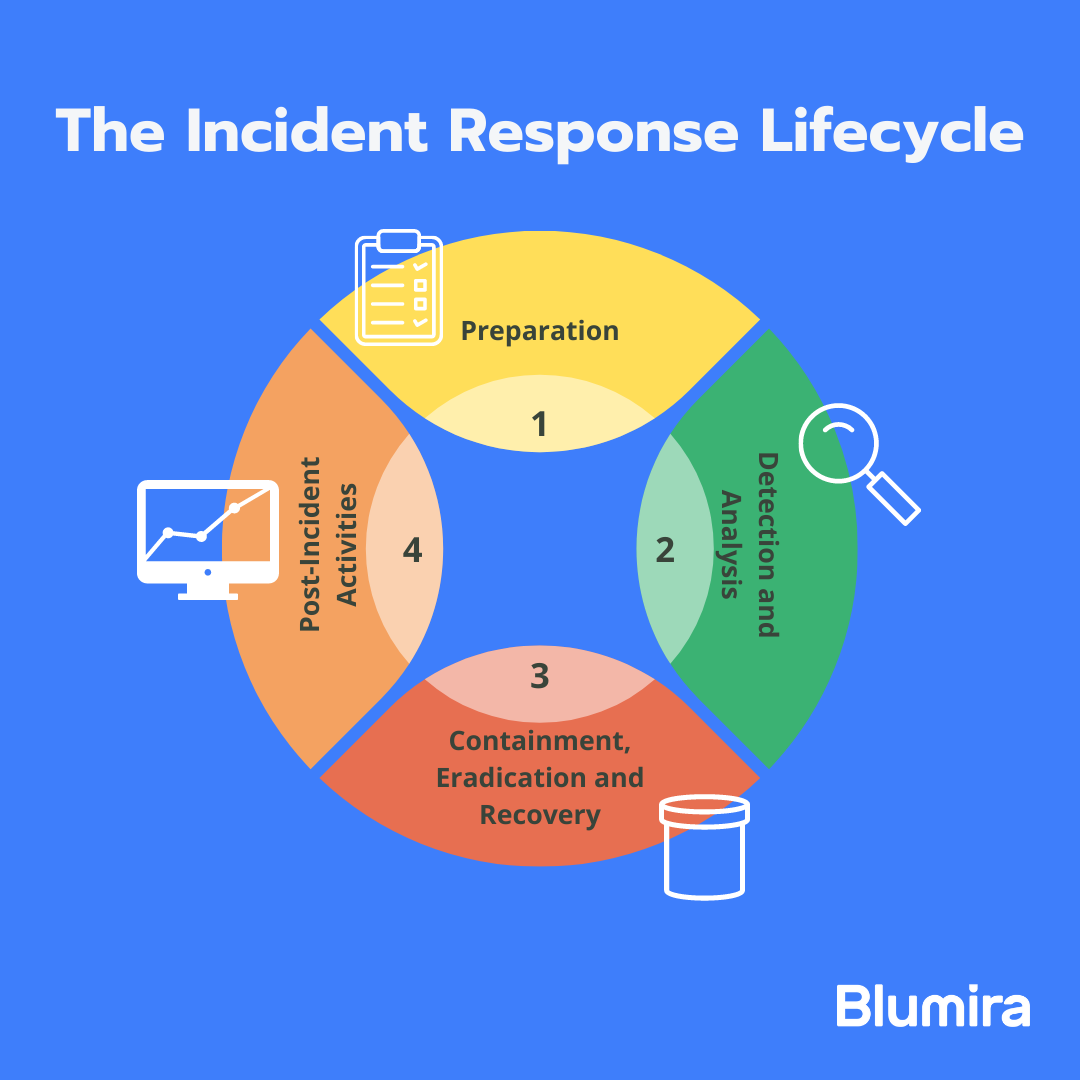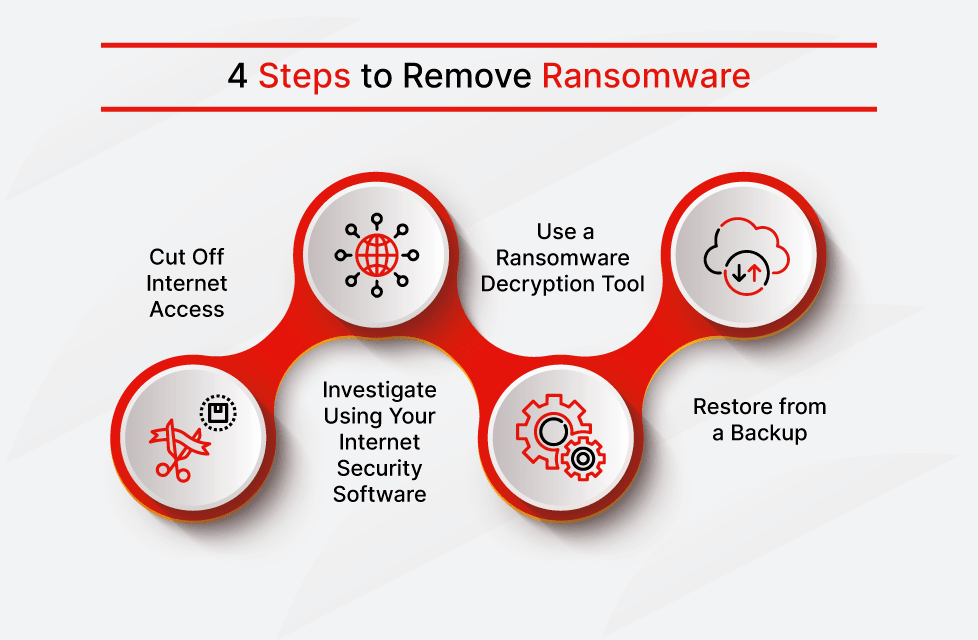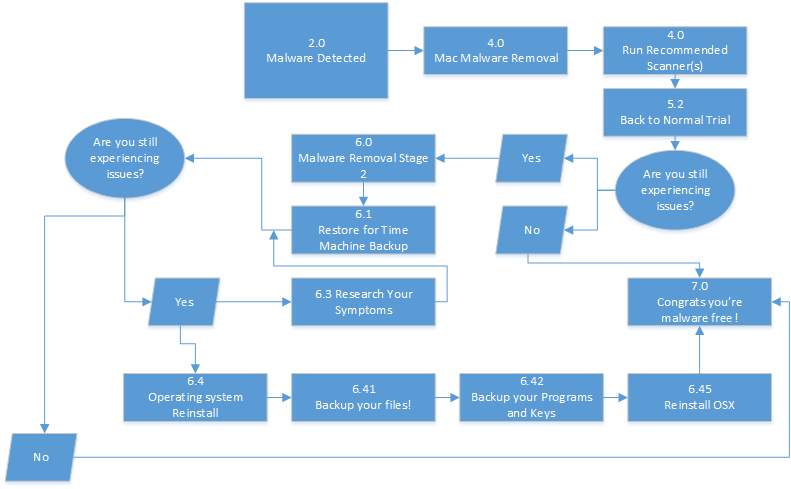
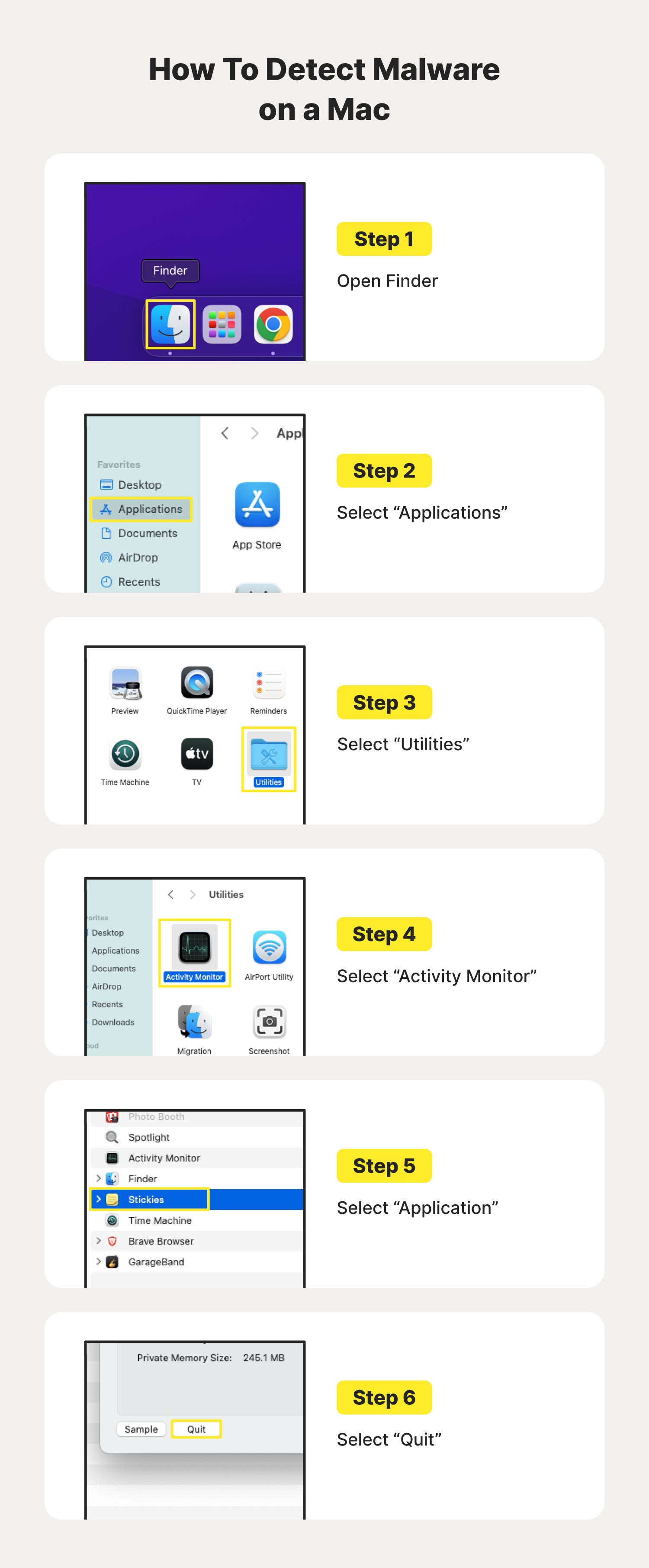
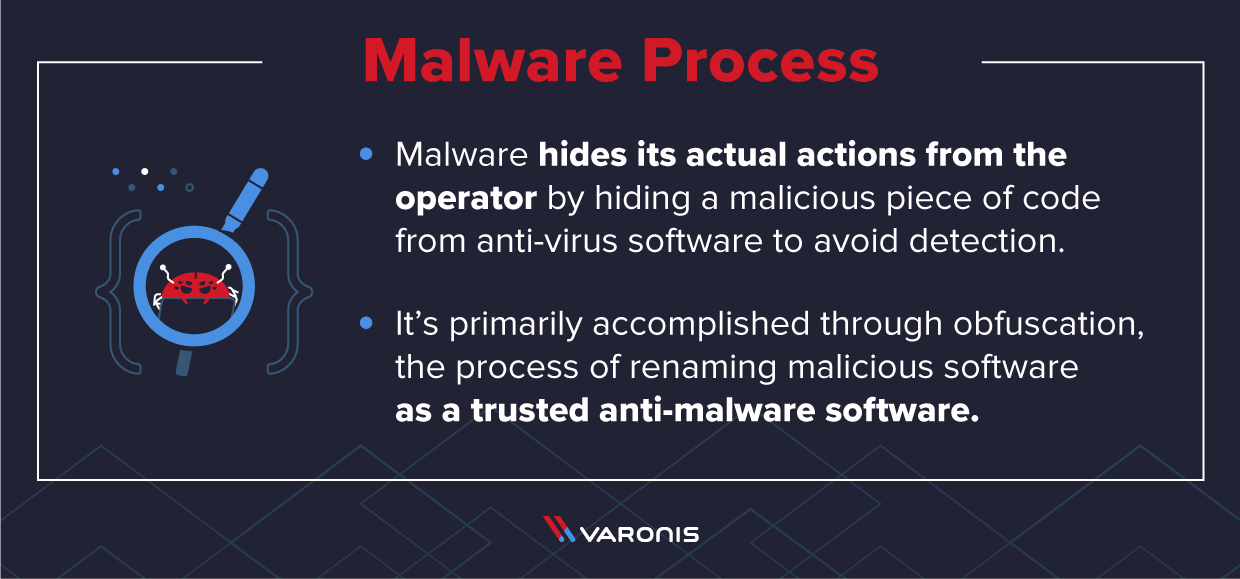
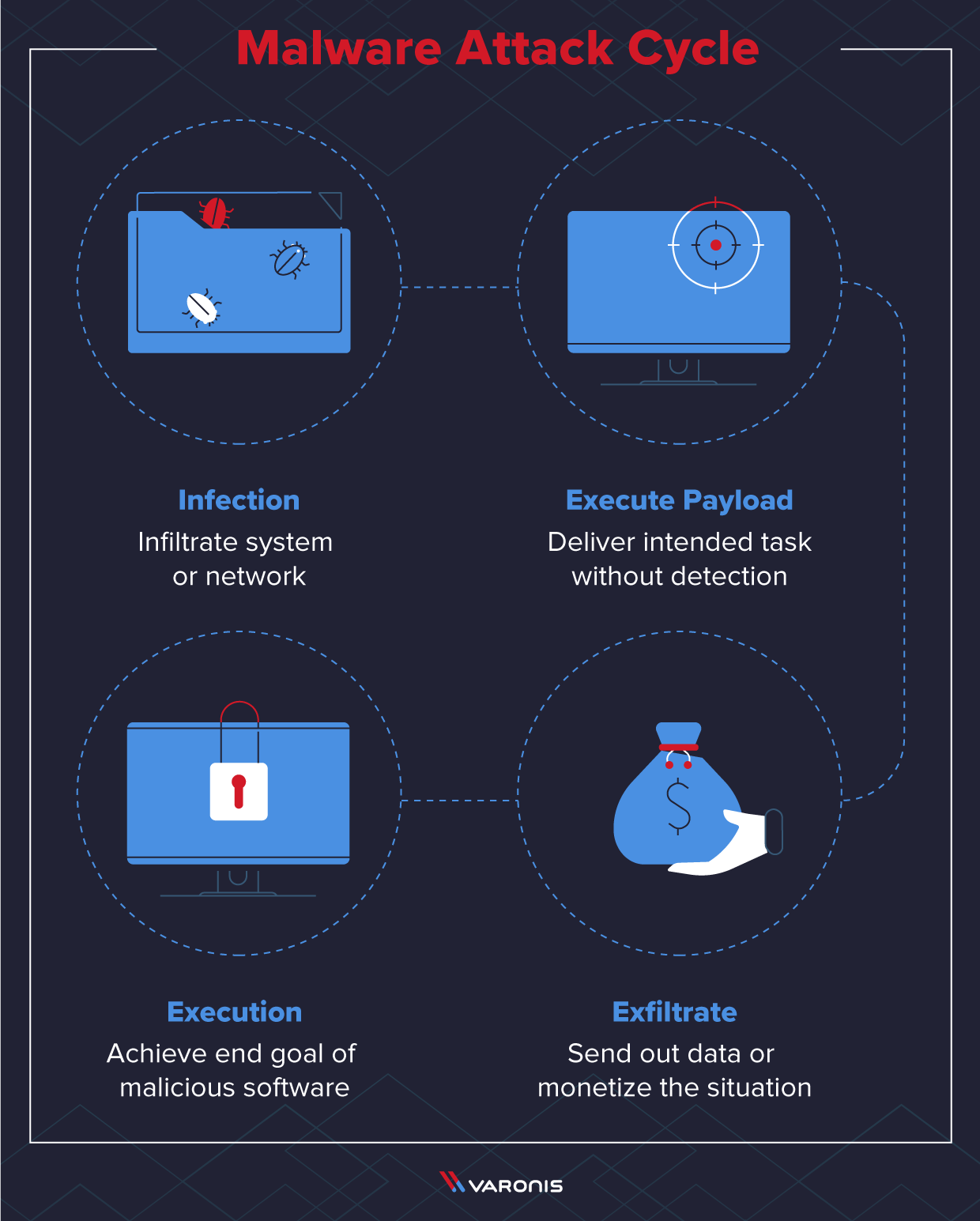
I've Got Malware, Now What? A Guide on Malware and Malware Removal | CAES Office of Information Technology

Best Practices for Malware Removal - CompTIA A+ 220-902 - 4.2 - Professor Messer IT Certification Training Courses
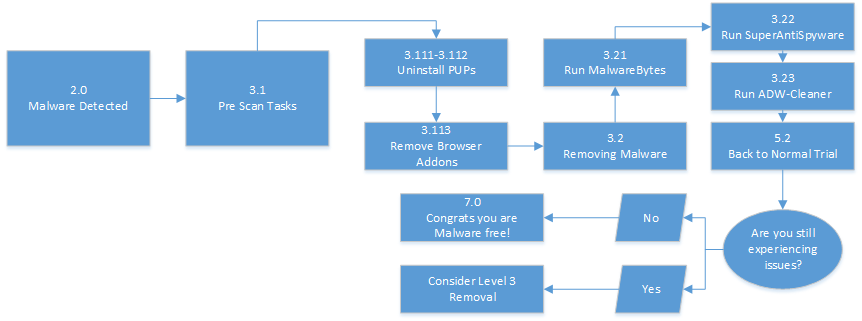
I've Got Malware, Now What? A Guide on Malware and Malware Removal | CAES Office of Information Technology
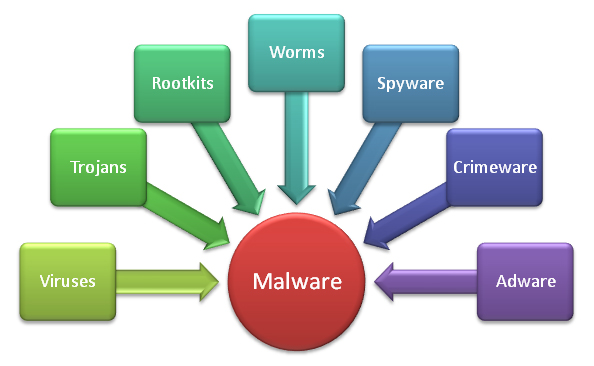
I've Got Malware, Now What? A Guide on Malware and Malware Removal | CAES Office of Information Technology
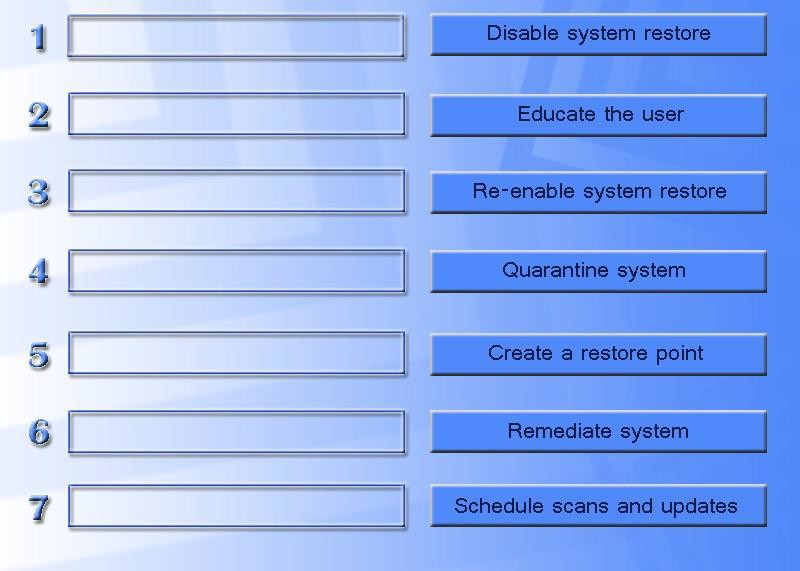



![Steps To Remove Malware From Wordpress Site [UPDATED] Steps To Remove Malware From Wordpress Site [UPDATED]](https://i0.wp.com/secure.wphackedhelp.com/blog/wp-content/uploads/2018/12/wordpress-malware-cleanup-steps-infographic.jpg?resize=574%2C2577&ssl=1)